Integrated Risk Analysis for large-scale Carbon Capture and Storage projects’ implementation
by Guillaume Kerlero de Rosbo

GHG (GreenHouse Gases) emissions have a variety of sources, but the first contributor today is the power generation industry, which accounts for more than one quarter of the total worldwhile emissions, and which represents approximatively 40% of all CO2 emissions in the EU.
To achieve sustainability regarding GHG emissions and to fulfill climate objectives, it is necessary for the international community not only to reduce our dependency to energy - which can be done by increasing energy efficiency or changing behaviours - but also to change our energy sources mix through a widespread use of renewable energies and/or nuclear.
However, energy needs are still increasing as new economical powers rise. Coal, probably being the most CO2 emitting fuel for power generation, still has strong reserves and some countries such as Poland, Germany or China deeply rely on this resource. Moreover, coal has the advantages to be cheap and quite well spread out, at a time when energy national self-sufficiency becomes more and more critical. For these reasons, power generation industry will surely continue to burn fossil fuels, especially coal, within the next decades. That is why it is essential to make coal-fired power plants cleaner, even if it is only for a transitional period.
In this context, Carbon Capture and Storage (CCS) technology is seen as one of the most promising solutions to cut CO2 atmospheric emissions down. According to the IEA (2008), CCS input could contribute to 19% of our reductions in CO2 emissions.
Carbon Capture and Storage entails returning the carbon issued from fossil fuel extraction and combustion to the subsurface, under the form of CO2. The solution consists of capturing CO2 from concentrated sources of emissions (power stations but also cement plants, refineries and steel mills) and separating it from the other gases. Then, it is compressed and conveyed to a geological repository. By procuring massive and immediate reductions in emissions, CCS provides a transitory solution concurrently with progress in energy efficiency and the development of other GHG-free forms of power generation .
In the framework of the European Economic Recovey Package (EERP), about 1.05 billion euros will be allocated to 7 large-scale CCS demonstration projects out of 13 short-listed candidates all across Europe. Two of them are already earmarked to receive respectively 100 and 50 million euro. Each one of the five other winners will receive 180 million Euro to kick-start the project.
Alstom Power is the world leader in turnkey integrated power plants solutions, equipment and associated services for the production of electricity. The company has developed solutions for a wide range of energy sources (coal, gas, nuclear, fuel-oil, hydropower, wind) and is a leader in innovative technologies for the protection of the environment (reduction of CO2 emissions, air quality control systems). One of the group priorities is thus to be at the forefront of carbon capture technology development and, since 2007, Alstom announced agreements with various companies to test CO2-capture technologies through pilot projects in the U.S. and Europe.
Among others, Alstom signed a contract with the Polish leader utility PGE (Polish Energy Group) to add a new 858 MW lignite-fired unit to the power plant of Belchatow (Poland), already being the biggest coal-based power plant in Europe and one of the biggest lignite-fired power plant in the world with more than 4400 MW capacity. The new power unit of 858 MW, planned to replace two ancient units, is already under construction and should be operational by end 2010 - early 2011. At the request of the customer, this unit has been re-designed as "capture ready", so that it could be later equipped with a CO2 capture system. In fact, PGE Belchatow plans to retrofit the new unit with a CCS plant, and has chosen Alstom to do so. GazoilProject, a subsidiary of the Polish Oil and Gas Company, will be responsible for the transport part, while the Polish Geological Institute and Schlumberger are in charge of the storage part. This project, planning to store 1.8 million tones of CO2 per year, is one of the 13 demonstration projects applying for the Recovery Package funding.
On 18 May 2009, the European Commission published the call for proposals for CCS projects in the framework of the European Recovery Plan. All applicants to the EERP funding had to submit their application forms by 15 July 2009. One of the key elements of the submission was to “provide evidence that all components of the proposal (base installation, CO2 capture, transport and storage) will be in place and that the project will be fully operational by the end of 2015, demonstrating the full chain from CO2 capture to storage” (UE Call for proposal), particularly through a particular section of the submission form, that should “identify the most significant [...] risks for the success of the project and describe contingency plans” (Grant application form).
In this context, I was responsible and project leader for this whole Risk Section of the submission form. My work at Alstom was thus to provide a general preliminary Risk Analysis for Belchatow large-scale CCS project, in direct relation with the leading entity of the project, PGE. The scope of work included not only Alstom’s capture part but all project phases (capture, transport and storage) and had to cover all risk aspects (technical, environmental, financial, project management, permitting and regulation, political and social acceptance). This objective was reached by building an innovative integrated risk analysis methodology and applying it to Belchatow’s case, all in two months time.
On the base of this work, the present article proposes a reference methodological tool allowing to quickly identify, assess and prioritize all types of risks that could threat any CCS project’s proper implementation, and to develop necessary adapted mitigation actions. Some ouputs from Belchatow exercice are given as examples and templates.
First, we will briefly describe what CO2 capture, transport and storage consist of and the new challenges it brings. Then, the risk analysis methodology will be presented before stressing main marches and lessons to learn from it .
CCS and critical issues
CCS is a broad term that encompasses a number of technologies divided in three different activities: capture of the CO2 (at the coal-fired power plant for example), transport of the CO2 to a suitable site and storage in a way that prevents the CO2 from returning to the atmosphere.
- CO2 capture is the process of removing carbon dioxide produced by hydrocarbon combustion (coal, oil and gas) before it is released to the atmosphere. There are currently three main methods of capturing CO2 referred as to post-combustion, oxy-combustion and pre-combustion.
- CO2 is then compressed to reach supercritical state (T>31°C, P>73 atm) before being transported to storage sites, either by tankers (on ships, trains or trucks) or pipeline for large volumes and long onshore distances. This supercritical state has transport properties (viscosity, diffusion) very close to gas and the density of a liquid, which makes it easier and cheaper to transport.
- Different potential geological sites exist to inject and effectively store CO2. Three of them have received extensive consideration: depleted oil and gas reservoirs, deep saline formations and unminable coal beds.
Different CCS steps and involved technologies show various states of maturity, current know-how being mainly inherited from Oil and Gas industry’s past activities, but CCS industry is still in its formative stages and all accumulated knowledge needs to be adapted, updated, spread-out and scaled-up to a commercial level. Moreover, the business association of these three very different industrial activities (running a fossil-fuel power plant, constructing and operating pipelines, and injecting gas underground) is very new for the Power Generation sector. CCS projects are thereby “first of their kind” not only from a technical point of view but also, to a certain extent, from a management point of view
Furthermore, the issue of the post-injection storage duration has to be addressed, as it poses some fundamental questions in terms of long-term environmental impact, long-term safety as well as long-term liability and site stewardship.
Then, apart from pure technical feasibility, three main issues still remain to be resolved in order to ensure technology deployment : financial competitivity, regulatory framework defintion and stability, and socio-political acceptance. As sources of uncertainty, these issues linked to the innovative status of the technology are also critical threats to any CCS project’s completion and need to be addressed through adapted risk analysis.
To sum-up, a CCS project is a very complex object, mixing different space and time levels, involving new associations. A CCS project, just as CCS deployment, has to face multi-dimensional issues mainly due to its rather innovative status.
That is why it is necessary to establish an adapted systematic framework to perform preliminary analysis of all the risks that could threaten such a project.
How to preliminary identify, assess, prioritize and mitigate all risks faced by a CCS project?
Use risk management and risk analysis concepts
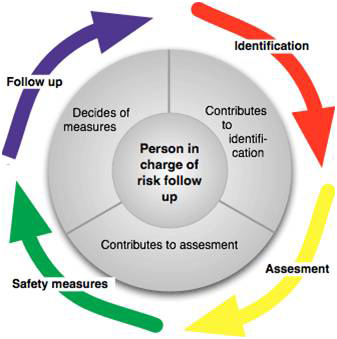
The global purpose of a risk management process is to plan, organize, lead, and control the activities of an organization or project in order to minimize the effects of risks on its objectives. It can also be defined through its main steps, such as illustrated on figure below.
Figure 1 : Risk Assessment principle, Source : Emeresse (2005)
A risk-optimized strategy relies on the use of risk analysis, which, after definition of the system and the way to model it, involves risk identification (discovering, defining and reporting risks in the most exhaustive way as possible), risk assessment (determining identified risks’ criticality through a measure of their likelihood to occur and the severity of their occurrence’s impacts, which allows to rank and prioritize risks), and definition of a risk mitigation plan (selecting options and actions to be taken in order to set risk at an acceptable level based on project constraints and objectives). Once risk analysis is carried out, actions must be implemented and risks communicated and followed-up in a proactive and iterative process.
Select and adapt existing risk methodological material
Risk analysis, and risk theory in general, has already been very much investigated in a wide range of activities and specialities. There already exist various recognized methodologies for analysing and assessing technological risks, financial risks, environmental impacts, and so on. But all these analysis often use very different approach, identification process, assessment and vocabulary.
Definition of risk itself is totally dependent on the context in which it is used. Indeed, it can non-exhaustively depend on the risk target (a territory, an ecosystem, a company, a project, a worker, or else), the risk owner or term user (an engineer, a modelist, a manager, a trader, etc.), the risk nature (health risks, financial risks, project risks, etc. Part of them, all of them). Depending on the case, risks can be defined as probabilities, losses, products of both, possibilities, events or conditions. In addition, risk is often employed undistinctively to other close notions such as uncertainty, threat, danger, hazard, issue, which add to its polymorpheous nature.
Considering the objective to ensure that everything is done to make a project successful and fully operational on time, appropriate definition is the one given in the PMBOK (Project Management Body of Knowledge) Guide, an internationnally recognized standard for project management. Risks are thus defined as “uncertain events that have the potential to negatively affect the project’s capacity to achieve its objectives and commitments, or that may cause an execution failure in the project. They are characterized by their probability to occur and the severity of their impacts.”
Moreover, current risk methodologies are almost always focused on a single factor and their conduct is very much scattered, each team or department launching its own risk analysis independently, consequently leading to separate efforts and reports. The aim of the following methodology is not to deny the already proven usefulness of these approaches, nor to substitute them, but to integrate some of the information they contain within a new approach providing a “risk knowledge base” for the capture, transport and storage of carbon dioxide. This leads to concentrated and gathered information preciously needed by the project management board, especially in the beginning of the project when it is the most important to identify and tackle risks. The methodological challenge is thus to select, adapt, and get inspired from parts of the existing material to find the most adapted formula to our specific objectives: obtain a quick, multi-dimension, and flexible tool that could be implemented since earliest stages of a project when some data is still missing or imprecise.
Model Risk system, identify and characterize risks: risk registers
Risks are not isolated entities and they have no fixed and definitive perimeters. All events have causes (or root-events) and consequences. They are part of scenarios, themselves shuffled within trees of events. This whole set of trees composes the risk system. There are two main simplified ways to represent this system: using trees or lists.
Tree analysis (Event Tree Analysis, Fault-Tree Analysis) displays the sequences of events involving success and/or failure of one system components. This representation is conceptually clearer and closest to the actual complexity of a system, but it needs the given malfunctioning or unwanted event to be defined a priori, which is incompatible with a genuine research for exhaustivity. Moreover, it demands a quantitative mathematical treatment later in the assessment which makes it quite heavy. We thus pitched on the check-list approach, gathering risk within several risk registers based on subdivisions of the following CCS risk system’s own representation.
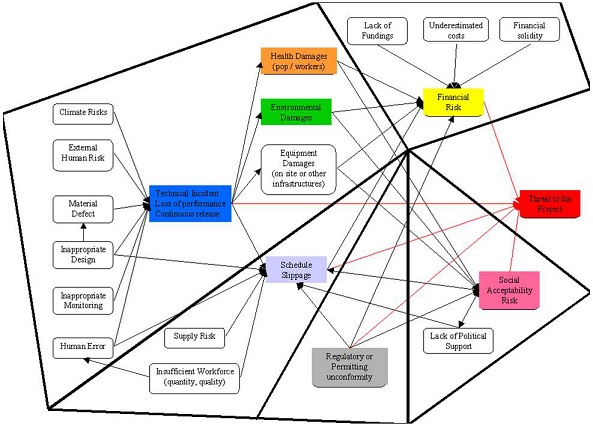
Figure 2 : Risk registers’ categorization, Source : Own figure
The different registers respectively focus on technical risks (lato sensu : includes some human and environmental risks mainly as consequences. It could be seen as a Health Security & Environment risk register), Financial risks, Organizational risks (management), Regulatory and permitting risks, and Social / Political support risks.
The main conceptual issue in listing risks is to find a way to reduce a multi-scenarios tree into a one dimension list. Each node of a risk scenario can be considered as an unwanted event, with an underlying risk. However, it is impossible to put each link of the chain in the relative dimension-focused table, as it would definitely be too laborious and more, it would lead to a number of needless repetitions along the different registers, assessing several times the same group of events, sometimes through the causes, sometimes through the consequences. Likewise, it would make the risk assessment very complex, as the probability assessment of a risk depends on the probability of its causes, and its impact assessment depends on the severity of its induced range of consequences.
Unfortunately, it is quite impossible to totally avoid this phenomenon. However it can be severely reduced by only reporting main links of the chains, minor parts being absorbed as causes or consequences of these main risks.
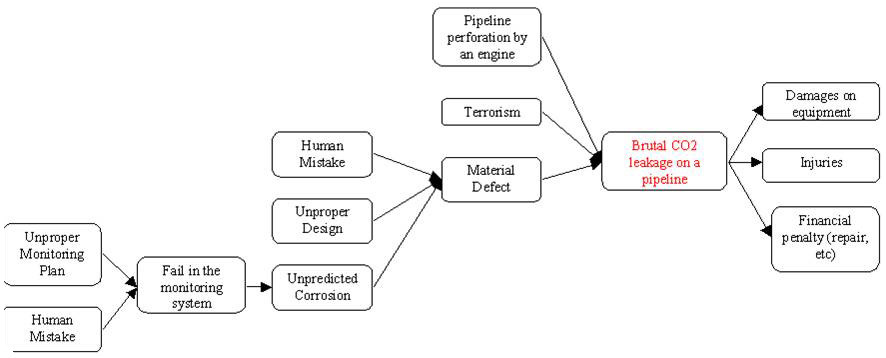
Figure 3 : Risk tree example, Source : Own figure
In the above example, the central event, the one we are really talking about in this non-exhaustive tree, is the leakage of CO2 (in red). Even if this risk involves a lot of dimensions, it remains, in the end, a technical issue. It will thus be reported in the technical risk register. Engine perforation, terrorism and material defect will be stated as potential causes, and damages on equipment, health, budget, or even on schedule and environment, as potential impacts.
Apart from risk description, potential causes and consequences, risk registers contain other information to characterize risks, such as risk active period (project phases when risk can occur) and existing or already planned safeguards (set of facts, actions and/or dispositions to prevent the risk occurrence or reduce its impacts).
Information needed to identify risks and characterize them is based on a benchmarking of existing and recognized aspect-specific risk methodologies, previous risk analysis, as well as knowledge taken from the whole CCS bibliograpy associated with personal brainstorming.
Assess all risks on a common basis: risk matrices and expert tells
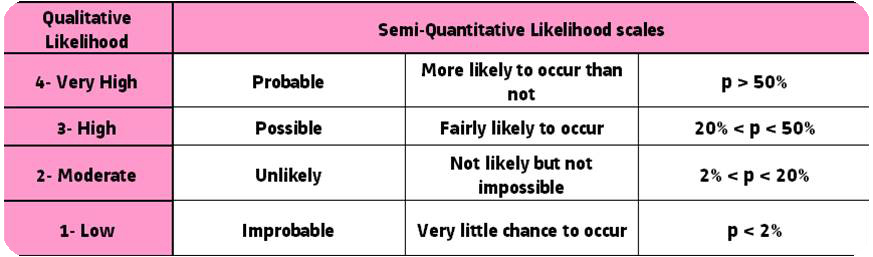
Risk assessment, i.e. measure of risk’s likelihood and impact(s) severity, can be either qualitative (using general qualificative categories such as “low”, “medium” or “high” for both likelihood and severity) or quantitative (using continous numeric scales), depending on level of detail needed, constraints such as available data, time, money and workforce dedicated to the analysis.
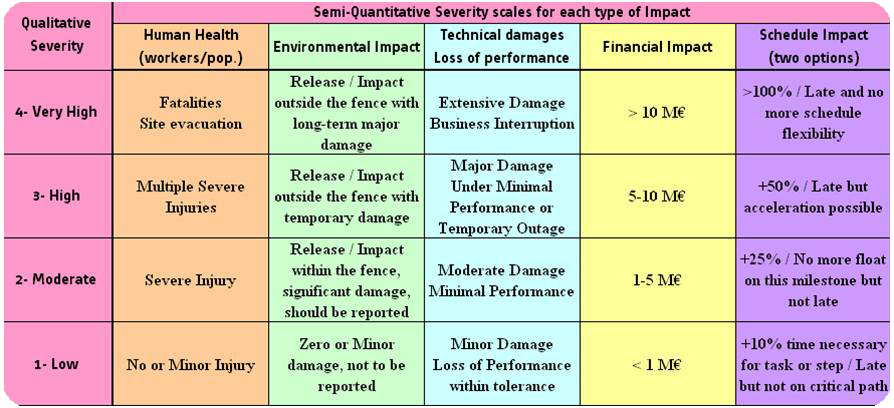
In a perspective of finding way to perform the most efficient risk analysis with minimum time, particularly in the initial stages of a project when data can be limited, qualitative option is much preferable. Moreover, qualitative measure is the only way to compare risks of different nature, as a common quantitative unit is almost impossible to determine. However, in an effort to enhance results’s precision and comparability, we can use an intermediate semi-quantitative approach, involving broad ranges of frequency or impact levels values in which the qualitative criteria (i.e. “moderate” gravity) is applicable. For the severity assessment, it can be done using several scales based on main types of impact the considered risk could lead to. Types of impact have been split into 5 categories (inspired from risk system’s representation, see figure 3) : impact to human health and safety (onsite workers and neighbouring populations), impact to environment, impact on equipment and production performance, impact on project’s financial safety and impact on schedule.
Here are the likelihood and severity assessment matrices constructed and used for Belchatow project.
Figure 4 : Likelihood assessment matrix – Belchatow example, Source : Own figure
Figure 5 : Severity assessment matrix – Belchatow example, Source : Own figure
So that all types of impacts are comparable and given same importance, severity matrix must comply with a “transversality” principle, i.e. that there is a global equivalence between all the factors being on the same line of the matrix (e.g. “high environmental impact” criteria being considered to be as severe as the “high financial impact”).
These two matrices aim at decreasing subjectivity contained in qualitative categories and estimate their actual criticality toward project’s objectives and alternatives (performance standards, budget restrictions, etc.). For this reason, likelihood and severity categories must be obligatory discussed and validated by the project’s management board (as they are the only ones to exactly know what is little or very critical to the project). Then, the more people involved in their elaboration the better.
Semi-quantitative risk assessment, as qualitative one, does not use any metrics, computing simulations or else. Then, assessment can only be done through human evaluation, involving analyst’s expertise, experience and perceptions. It is a typical use of “expert tells”. Due to the scope and the multi-disciplinary nature of the CCS risk analysis, a team effort is needed to produce the desired outcome. The quickest way to efficiently gather people’s knowledge is to set up thematical risk workshops, involving different experts and managers from the different companies participating to the project, where these key people could discuss, brainstorm, and commonly assess risks previously compiled in the different risk registers.
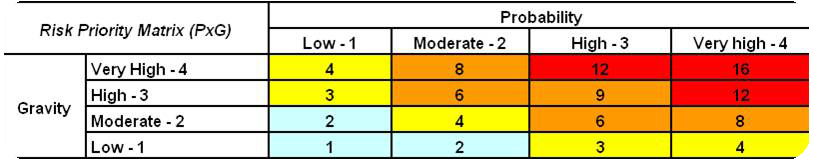
On the base of these evaluations, a criticality score (or risk priority number, as used in FMEA methodology) is given to each risk, multiplying values from 1 to 4 given to both likelihood and severity categories. This can be done using a risk criticality or priority matrix such as presented on figure 6.
Figure 6 : Risk priority matrix – Belchatow example, Source : Own figure
This enables to compare risks against each other and allows us to understand the total level of risk facing the program at any given time. This can also serve as a base for risk mapping representation (risks likelihood and severity respectively charted on the X- and Y-axis).
Define appropriate mitigation actions : response level’s formalization
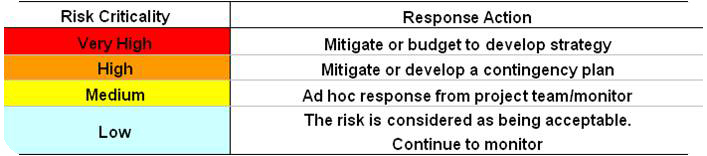
Once individual risks have been attributed a criticality score, it is possible to establish formalised actions based upon the risk grading. Setting up a formalised level of risk answer is deeply dependent on the determination of the level of risk acceptability (e.g. “only Low risks are acceptable”). The higher the score, the stronger the needed response to set the risk below the acceptability threshold.
Figure 7 : Response matrix – Belchatow example, Source : Own figure
Again, management board’s judgment is needed in setting the color code to stick with the special situations of each project.
All mitigation actions from all registers are then aggregated to form the Mitigation Plan.
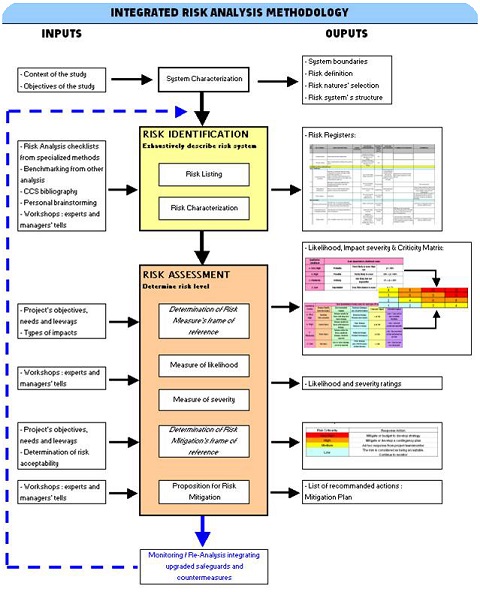
Figure 8 summarizes the whole integrated preliminary risk analysis process we have been detailing along this second chapter. The blue part shows how this articulates with the rest of risk management.
Figure 8 : Risk analysis methodology’s Sum-up diagram, Source : Own figure
Conclusions
Apart from general benefits of risk analysis, such as a common understanding of the panel of risks the project is exposed to as well as an increased chance that the objectives of the program will be met thanks to the identification of improvement areas and determination of needed mitigation actions, this particular type of method has more specific interests:
- It is multi-issue: the whole project’s risk system is represented, which is not the case of most of existing specialized methods.
- It is multi-usage: the results can be examined as a whole by the management board, using risk mapping or risk repartition, but it can also be used by different department managers and specialists, focusing on dimension-specific risk registers and developing separate aspect-specific risk maps.
- It is relatively simple and quick: a first-approach risk picture of the project can be obtained in a little time with few data, which is not the case of any quantitative method.
- It is flexible: the methodology has been designed for earliest stages of a project ; it can thus deal with quite imprecise data. This allows pointing out the necessity for major changes to philosophy/design before significant financial commitments are made. But it can, and must, also be used during further steps of the project, getting more and more precise as data come out.
- It is collaborative: people from all parts of the project are involved, experts and managers from all the participating companies, which give more legitimacy to the results, better understanding and increased self-motivation among employees.
From another point of view, this procedure can face certain degree of subjectivity, lack of precision and impossibility to ensure exhaustivity. Subjectivity is due to the matrices being determined by project‘s management board and risk assessment being based on human expertise. Lack of precision mainly comes from the discrete (non-continous) nature of likelihood, severity and criticality categories.
Subjectivity of matrix determination and risk measure, as well as potential lack of registers’ exhaustivity can be reduced by involving every key persons (experts and managers, through workshops or interviews) in both risk identification and assement framework’s characterization, and by progressing in a “learning by doing” iterative way, building draft registers/matrices and testing them in operational conditions.
Lack of precision related to semi-quantitative approach is actually not really a problem, as the objective to provide a preliminary risk screening and mapping necessitates to think in terms of “risk area” (within criticality grid or risk map) more than in terms of “absolute risk value”. If a risk is highly critical, only thing we need to know is that it is in the unacceptable area and that strong actions must be implemented. It is not vital to know its very precise value. Where more details can be needed, and further studies carried out, is for risks located around the acceptability frontier, or in order to improve precision of some high risks’ criticality in order to help select most appropriated mitigation measures. In such cases, the methodology can be fed by additional data coming from additional studies or quantitative modeling tools.
This methodology is aimed at ensuring consistency of results in any context, ensuring comparability of all types of issues and corresponding solutions, providing all necessary elements to help management board adopt a risk-optimized strategy, as well as all relevant data to communicate and defend related decisions. This includes relevant risk system’s representations as well as adapted action plans.
It should certainly not be considered as a way to obtain a single one-shot picture of the project risks, which we go through at the beginning of the project before forgetting it or basing long-term strategy on it. Risk system is a polymorphous and moving notion and risk analysis must be regularly updated during the course of the project based on actual inputs
Finally, this methodology can be used by any company leading or involved in any large-scale industrial project. Companies involved in CCS projects will additionally benefit from outputs resulting from the methodology’s application to Belchatow project, risk registers and risk matrix being given as templates.
Par Guillaume Kerlero de Rosbo
Septembre 2010